The Advanced Encryption Standard (AES) has become a popular cryptographic specification in many applications, such as applications in embedded systems. Since the National Institute of Standards and Technology (NIST) selected this specification as a standard specification in 2002, developers of processors, microcontrollers, FPGAs, and SoC applications have used AES to protect inputs, outputs, and systems. data. We can describe algorithms very efficiently at a higher level of abstraction, as used in traditional software development; but because of the operations involved, the algorithm is most efficient to implement in an FPGA. Developers can even get some "free" access in the cabling.
For these reasons, AES is a great example of a developer who can use the C language to describe the algorithm and then accelerate it in hardware to benefit from the Xilinx SDSoC? Development environment. In this article we are going to do this, first familiarize yourself with the AES algorithm, then at Xilinx Zynq? The A7000256 (256-bit key length) is implemented on the -7000 All Programmable SoC's processing system (PS) to establish a software performance benchmark and then accelerate in on-chip programmable logic (PL). To fully understand the benefits available, we will perform these steps in all three operating systems supported by the SDSoC environment: Linux, FreeRTOS, and bare metal.
algorithmAES is a symmetric block cipher that can use different key lengths of 128, 192, and 256 bits. The length of the key determines the number of processing steps required to encrypt or decrypt the data. As the name implies, the block cipher algorithm uses data blocks. The AES algorithm processes a fixed block of 16 bytes at a time. Therefore, if our password content is less than 16 bytes, we must fill in unused bytes.
Since AES is a symmetric cipher, the same practices and secrets are used for both information encryption and decryption. In contrast, asymmetric algorithms (such as RSA) use different keys for data encryption and decryption.
Each of the four phases in the AES algorithm represents a state. The combination of the four AES phases is called a loop. The number of cycles required depends on the length of the key.
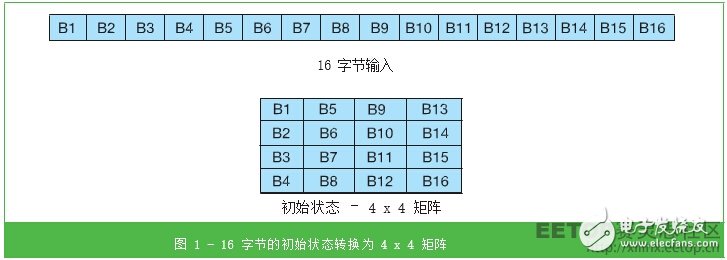
Quite simply, the AES state starts at the 16 bytes we want to encrypt. Each new step updates the status. Before processing the state, we need to change the input byte string to the initial state, the 4 x 4 matrix (Figure 1).
Plug-In Connecting Terminals,Insulated Spade Terminals,Cable Connector Double Spade Terminals,Vinyl-Insulated Locking Spade Terminals
Taixing Longyi Terminals Co.,Ltd. , https://www.lycopperterminals.com