Recently, in the field of biometric identification, there has been a surge in the use of fingerprint authentication as a simple but secure method to access and protect data. This method is also playing an increasing role in secure electronic and mobile transactions.
Compared with requiring users to create, remember, and protect passwords, fingerprint authentication is much safer and easier to use for user authentication, so fingerprint authentication has become the preferred method for merchants, banks, users, and third-party settlement agencies. Some technological advancements and active innovations made by industry-leading companies in the field of fingerprint identification have produced several different forms of fingerprint identification methods, but these methods are fundamentally different.
Not all fingerprint authentication technologies are "born equal"
The phrase "All men are created equal" is highly praised by the statement made by Thomas Jefferson, the third president of the United States, in the "Declaration of Independence." Although this concept of equality has a long history, it is not necessarily applicable to biometric security technology, because not all fingerprint authentication technologies are “born equalâ€.
In the field of biometrics, fingerprint authentication technology is used to protect the security of the device and the data accessed by the device, and to ensure the security of transactions. Although fingerprint recognition technology has been widely used in the above fields, its similarity is limited to this. The technology behind fingerprint authentication is different, as is the level of security it can provide.
A common fingerprint verification technology is the Match-on-Host technology on the main chip; after using this technology, the fingerprint sensor reads the fingerprint data and sends it to the main processor or other external processor for processing. Although the fingerprint data is acquired by the fingerprint sensor, all processing and matching work is done on the main control platform. Another fingerprint verification technology is Match-in-Sensor technology. This technology uses a customized, fully packaged single-chip system (SoC) architecture to register fingerprints and patterns within the actual fingerprint sensor module. Storage and biometric matching are isolated.
Let's take a look at the essential difference between these two very different fingerprint verification methods.
Matching on main chip: current standardThe basic requirement of fingerprint sensing is to clearly identify the user by matching with a known and secure "template" or record of the user's fingerprint (Figure 1). The sensor is initially used to capture data and create a user record during the "registration" process. After that, each time the user attempts to access the device, the sensor will obtain fingerprint data and compare it with the stored template.
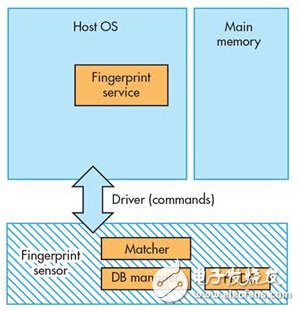
Currently, almost every fingerprint sensing solution performs matching operations directly on the main system, whether it is a smartphone, tablet, PC, or a dedicated device customized for security. Therefore, the matching architecture on the main chip is to use two ICs-one is a sensor IC used to obtain data, and the other is an independent controller IC used to run the actual matching operation software (usually application processing on mobile devices Device)-to meet the functional requirements.
Any new technology will naturally use the main chip resources as a starting point. Therefore, the first generation fingerprint sensor is a very simple device, limited to completing a single task, that is, collecting fingerprint data, and then the software running in the main chip uses these fingerprint data to verify the user's identity.
The functions performed by the software include: identifying fingerprint features, establishing secure biometric resources (fingerprint templates), storing fingerprint templates, and matching the newly created fingerprint templates with the fingerprint templates already stored on the device. The main system also provides the security needed to protect the integrity and privacy of fingerprint data. In addition, the main system is also responsible for detecting counterfeit biometric data-these so-called anti-spoofing techniques are necessary to contain the presentation attack (presentaTIon attack).
The two main selling points of the matching architecture on the main chip are low cost and short design-in time, which allows fingerprint sensing to be added to the device more quickly and cost-effectively. This momentum has in turn promoted progress in related areas, such as the Universal Authentication Framework (UAF) established by the FIDO (Fast Online Authentication) Alliance. However, despite its many advantages, when it comes to providing true security, the matching method on the main chip dwarfs the matching architecture within the sensor.
In-sensor matching architecture: next-generation standardAs the name implies, the matching architecture within the sensor integrates matching and other biometric management functions directly into the sensor IC. The IC contains high-speed microprocessors, instruction and data storage, secure communications and high-performance encryption. In order to achieve this level of integration while establishing a secure execution environment within the sensor IC, the sensor matching technology uses an SoC architecture (Figure 2).
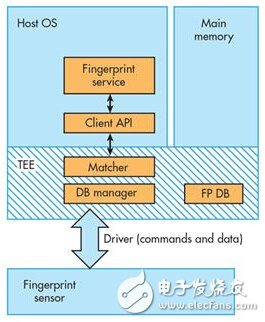
Because the integration of multiple functions is the reason for the existence of integrated circuits, this progress does not seem to be called the "next generation" progress. However, fully integrated sensing and matching functions can significantly enhance safety, and this alone is sufficient to conclude that its expected industry influence cannot be underestimated.
The advanced security of the matching architecture in the sensor can be applied to both the system and the protection of the user's unique biometric information. The following advances have enhanced system-level security:
The execution environment of fingerprint data and fingerprint matcher is physically isolated from the main chip operating system, so it can resist hacker or malware attacks on the main chip.
The sensor performs the biometric recognition function independently, without relying on the input of the main chip, thus avoiding the damage that may be caused if the main chip is in danger.
The input parameter of the matcher is living fingerprint information-the sensor chip and its registered template obtain this information, and encrypt and process it.
Can accurately verify the authenticity, because the recognition result is signed by the private key of the sensor from the hardware.
The creation, storage, and management of keys representing identity credentials are shared—these keys are also used to sign certificates to prevent damage from malicious software with false information.
Even if the main chip is successfully broken by any type or source of attack, it is extremely difficult to force the matcher to produce false positive results, re-provide previous results, or change or manipulate the matching results in any other way. This ensures that even in the worst case, the authentication subsystem is still safe.
As for the user's biometric information, protection is enhanced by the following characteristics. First, fingerprint data, including all the characteristics / features extracted from it and all established templates, are only processed in the on-chip CPU and memory of the sensor. This information will never be shared with or exposed to the master device. In addition, the registration database is located in a separate flash memory, isolated from other parts, and only sensors can be physically accessed. In addition, the registration template is encrypted and signed by the sensor using a proprietary algorithm and a strong key before being stored in the independent flash memory.
Like the system-level security discussed earlier, even if the main chip is completely destroyed by some successful attack, the attacker cannot extract any biometric information of the user, and the theft of biometric information is undoubtedly the most destructive imaginable One of the forms of identity theft.
SynapTIcs provides the industry's first fingerprint sensor fully encapsulated in hardware, which allows customers to provide extremely strong protection in their products. At the same time, SynapTIcs is the only company in the industry that provides this solution. The matching solution in the sensor stores the collected and managed data in the sensor itself-completely isolated from the main system, thus avoiding the problem that the main system is vulnerable to hackers. The sensor also does not store a real fingerprint image, but creates a template that is encrypted using 256-bit Advanced Encryption Standard (AES) technology and cannot be reconstructed. Even if the main system encounters a security threat, the biometric data is still safe because it is always located in the fingerprint sensor module.
In-sensor matching technology can provide powerful and safer protection than the main chip for many applications, such as smartphones, tablets, personal computers, computer mice and keyboards, docking stations, and automobiles. At present, in order to protect the security of e-commerce, financial transactions and medical care records, relevant legislative work is in progress, so companies urgently need to use sensor matching technology to meet strict laws and regulations.
SynapTIcs provides sensors using this new sensor matching technology, which has enabled Synaptics to gain a significant lead in biometric data security. As new in-sensor matching solutions are used more and more, people will more and more clearly see that although different biometric matching technologies seem similar, not all fingerprint authentication technologies are born. equality".
in conclusionThe support of the ecosystem including fingerprint authentication technology is steadily increasing, and at the same time, Synaptics has developed advanced in-sensor matching solutions. These solutions have passed FIDO certification, can read fingerprint information from various angles, choose whether to provide visual or tactile feedback information, and are optimized for devices or applications. In addition, matching within the sensor does not require biometric information to be transferred or shared between the fingerprint module and the host device, so even if the system is compromised, there is no risk of theft of biometric data.
Therefore, if you think that all fingerprint authentication technologies are the same, then you may need to spend some time to understand the matching architecture and its functions in the sensor.
Portable power system ,Portable power storage,Portable solar system, Outdoor power station, Portable power station
SHENZHEN CHONDEKUAI TECHNOLOGY CO.LTD , https://www.szfourinone.com